Friday, August 16, 2013
[TIP] Android emulator works nice and fast,
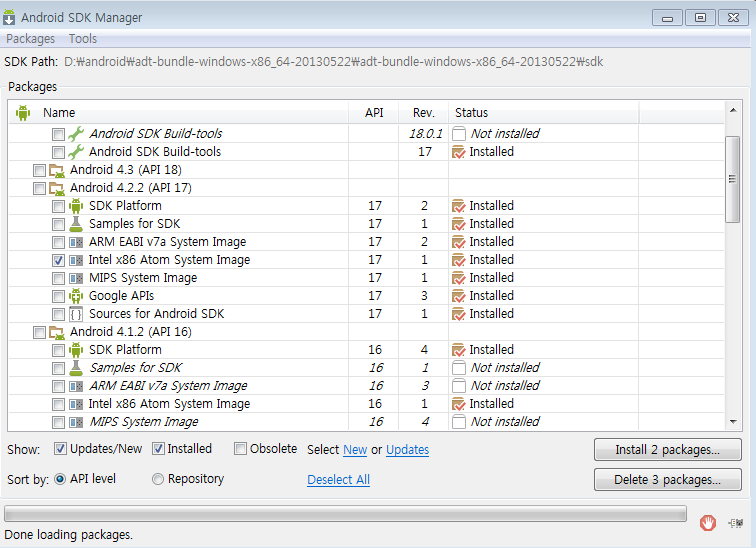
[problem]
On Windows, emulating RAM greater than 768M may fail
depending...
Try proqressively smaller values of RAM if the emulator fails
to launch
[resolved]
install 'Intel x86 Atom System Image'
Tuesday, July 23, 2013
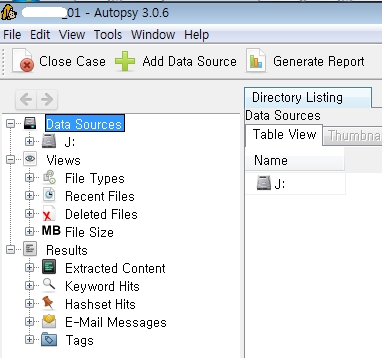
Create an image file and Autopsy...
If you want to get a hard image attaced to the slave, do as follows:
dd if=\\?\Device\Harddisk1\Partition0 of=IMAGE001.img bs=512
Load the image file by Autopsy.
Analyze the image~
슬레이브로 붙인 하드 이미지를 뜨고 싶으면 아래와 같이 하면 된다.
dd if=\\?\Device\Harddisk1\Partition0 of=IMAGE001.img bs=512
그럼 이 이미지 파일을 오토시(autopsy)에 불러들여
포렌식 분석을 하시면 된다.
dd if=\\?\Device\Harddisk1\Partition0 of=IMAGE001.img bs=512
Load the image file by Autopsy.
Analyze the image~

슬레이브로 붙인 하드 이미지를 뜨고 싶으면 아래와 같이 하면 된다.
dd if=\\?\Device\Harddisk1\Partition0 of=IMAGE001.img bs=512
그럼 이 이미지 파일을 오토시(autopsy)에 불러들여
포렌식 분석을 하시면 된다.
Thursday, July 11, 2013
[Tips] Load Symbol
Case 1. code snippet
symPath[] = "symsrv*symsrv.dll*c:\symbol*http://msdl.microsoft.com/download/symbols";
SymInitialize(hProcess, &symPath, TRUE);
http://msdn.microsoft.com/en-us/library/windows/desktop/ms681351(v=vs.85).aspx
Case 2. Using Windbg 1
[File] - [Symbol File Path ...]
enter the symbol
srv*c:\symbol*http://msdl.microsoft.com/download/symbols
Then open an executable or ...
Case 3. Using Windbg 2
open an executable or attach ...
(d4.7f0): Break instruction exception - code 80000003 (first chance)
eax=001a1eb4 ebx=7ffdc000 ecx=00000000 edx=00000001 esi=001a1f48 edi=001a1eb4
eip=7c90120e esp=0007fb20 ebp=0007fc94 iopl=0 nv up ei pl nz na po nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000202
ntdll!DbgBreakPoint:
7c90120e cc int 3
0:000> .sympath srv*c:\syms*http://msdl.microsoft.com/download/symbols
Symbol search path is: srv*c:\syms*http://msdl.microsoft.com/download/symbols
Expanded Symbol search path is: srv*c:\syms*http://msdl.microsoft.com/download/symbols
0:000> .reload /f *
심볼 설정할 때 코드로 짜기도 하고 windbg 로 설정하기도 한다.
상황에 맞게 적절히 사용~
symPath[] = "symsrv*symsrv.dll*c:\symbol*http://msdl.microsoft.com/download/symbols";
SymInitialize(hProcess, &symPath, TRUE);
BOOL WINAPI SymInitialize( _In_ HANDLE hProcess, _In_opt_ PCTSTR UserSearchPath, _In_ BOOL fInvadeProcess );
http://msdn.microsoft.com/en-us/library/windows/desktop/ms681351(v=vs.85).aspx
Case 2. Using Windbg 1
[File] - [Symbol File Path ...]
enter the symbol
srv*c:\symbol*http://msdl.microsoft.com/download/symbols
Then open an executable or ...
Setting Symbol and Executable Image Paths in WinDbg
http://msdn.microsoft.com/en-us/library/windows/hardware/hh439335(v=vs.85).aspxCase 3. Using Windbg 2
open an executable or attach ...
(d4.7f0): Break instruction exception - code 80000003 (first chance)
eax=001a1eb4 ebx=7ffdc000 ecx=00000000 edx=00000001 esi=001a1f48 edi=001a1eb4
eip=7c90120e esp=0007fb20 ebp=0007fc94 iopl=0 nv up ei pl nz na po nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000202
ntdll!DbgBreakPoint:
7c90120e cc int 3
0:000> .sympath srv*c:\syms*http://msdl.microsoft.com/download/symbols
Symbol search path is: srv*c:\syms*http://msdl.microsoft.com/download/symbols
Expanded Symbol search path is: srv*c:\syms*http://msdl.microsoft.com/download/symbols
0:000> .reload /f *
심볼 설정할 때 코드로 짜기도 하고 windbg 로 설정하기도 한다.
상황에 맞게 적절히 사용~
Friday, July 5, 2013
[Threat] Android Defender
| Symantec | Android.Fakedefender |
Permissions
Activate Device Administrator
- Erase all data
- Change the screen-unlock password
- Set password rules
- Monitor screen-unlock attempts
- Lock the screen
안드로이드용 악성코드 중 재미있는 가짜백신이 발견되었는데
랜섬웨어(ransomware)이며 조치가 까다롭다.
Tuesday, June 25, 2013
[DEV] [TIP] Visual Studio :: Character set error
error C2664: '_stricmp' : cannot convert parameter 1 from 'LPCTSTR' to 'const char *'
This error is caused by Character set. The default character value is "Unicode" running VS 2005 or later
To solve this, change the "character set" field to multibyte
=> project property -> property -> configuration property
비주얼 스튜디오 컴파일할 때 문자열 셋팅 때문에 에러가 나는 경우가 있다.
2005 이상부터는 unicode 문자열로 셋팅되어 있어서 멀티바이트로 셋팅해 주어야
컴파일이 된다.
Thursday, May 30, 2013
MS13-034 [CVE- 2013-1347]
http://blogs.technet.com/b/msrc/archive/2013/05/03/microsoft-releases-security-advisory-2847140.aspx
http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1347
Microsoft Internet Explorer 8 does not properly handle objects in memory, which allows remote attackers to execute arbitrary code by accessing an object that was not properly allocated or is deleted, as exploited in the wild in May 2013.
한국의 대부분 사용자들이 IE를 사용하는데 IE 취약점이라 위험성이 크고
이를 이용해 정보유출을 시도하는 케이스들이 발견되고 있으니
반드시 패치를 하시길!
Obfuscated javascript
Decoded javascript
MS IE 8 Vulnerability
http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1347
Microsoft Internet Explorer 8 does not properly handle objects in memory, which allows remote attackers to execute arbitrary code by accessing an object that was not properly allocated or is deleted, as exploited in the wild in May 2013.
한국의 대부분 사용자들이 IE를 사용하는데 IE 취약점이라 위험성이 크고
이를 이용해 정보유출을 시도하는 케이스들이 발견되고 있으니
반드시 패치를 하시길!
Obfuscated javascript
Decoded javascript
MS IE 8 Vulnerability
Wednesday, May 29, 2013
Sunday, April 14, 2013
Kernel Memory Dump Analysis
windbg로 커널 메모리 덤프를 분석해야 할 때...
Kernel memory dumps are located in %systemroot%\MEMORY.DMP
(%systemroot%\minidump)
1. Open the MEMORY.DMP file using Windbg.
(Symbol setting : SRV*c:\[path]*http://msdl.microsoft.com/download/symbols)
2. Enter '!analyze -v' without quotes to get detailed debugging information.
KERNEL_DATA_INPAGE_ERROR (7a)
The requested page of kernel data could not be read in. Typically caused by
a bad block in the paging file or disk controller error. Also see
KERNEL_STACK_INPAGE_ERROR.
...
SYMBOL_NAME: volmgrx!VMX_NOTIFICATION_
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: volmgrx
IMAGE_NAME: volmgrx.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 49e01efd
FAILURE_BUCKET_ID: 0x7a_c000000e_volmgrx!
3. What process was calling volmgrx.sys?
kd> !thread
THREAD 9b75f2b0 Cid 18e4.1754 Teb: 7ffdb000 Win32Thread: ffb9f540 RUNNING on processor 1
IRP List:
872f9290: (0006,01d8) Flags: 00060000 Mdl: 00000000
Not impersonating
DeviceMap 8d405780
Owning Process 8abb30e0 Image: vds.exe
Attached Process N/A Image: N/A
Wait Start TickCount 153296998 Ticks: 0
Context Switch Count 205
UserTime 00:00:00.000
KernelTime 00:00:00.171
Win32 Start Address 0x76c70148
Stack Init 8c315000 Current 8c314978 Base 8c315000 Limit 8c312000 Call 0
Priority 10 BasePriority 8 PriorityDecrement 0 IoPriority 2 PagePriority 5
...
4. Confirm that vds.exe process called the volmgrx.sys...
kd> !process 8abb30e0 0
PROCESS 8abb30e0 SessionId: 0 Cid: 18e4 Peb: 7ffd6000 ParentCid: 0294
DirBase: bff34bc0 ObjectTable: 9a5556f0 HandleCount: 193.
Image: vds.exe
...
Kernel memory dumps are located in %systemroot%\MEMORY.DMP
(%systemroot%\minidump)
1. Open the MEMORY.DMP file using Windbg.
(Symbol setting : SRV*c:\[path]*http://msdl.microsoft.com/download/symbols)
2. Enter '!analyze -v' without quotes to get detailed debugging information.
KERNEL_DATA_INPAGE_ERROR (7a)
The requested page of kernel data could not be read in. Typically caused by
a bad block in the paging file or disk controller error. Also see
KERNEL_STACK_INPAGE_ERROR.
...
SYMBOL_NAME: volmgrx!VMX_NOTIFICATION_
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: volmgrx
IMAGE_NAME: volmgrx.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 49e01efd
FAILURE_BUCKET_ID: 0x7a_c000000e_volmgrx!
3. What process was calling volmgrx.sys?
kd> !thread
THREAD 9b75f2b0 Cid 18e4.1754 Teb: 7ffdb000 Win32Thread: ffb9f540 RUNNING on processor 1
IRP List:
872f9290: (0006,01d8) Flags: 00060000 Mdl: 00000000
Not impersonating
DeviceMap 8d405780
Owning Process 8abb30e0 Image: vds.exe
Attached Process N/A Image: N/A
Wait Start TickCount 153296998 Ticks: 0
Context Switch Count 205
UserTime 00:00:00.000
KernelTime 00:00:00.171
Win32 Start Address 0x76c70148
Stack Init 8c315000 Current 8c314978 Base 8c315000 Limit 8c312000 Call 0
Priority 10 BasePriority 8 PriorityDecrement 0 IoPriority 2 PagePriority 5
...
4. Confirm that vds.exe process called the volmgrx.sys...
kd> !process 8abb30e0 0
PROCESS 8abb30e0 SessionId: 0 Cid: 18e4 Peb: 7ffd6000 ParentCid: 0294
DirBase: bff34bc0 ObjectTable: 9a5556f0 HandleCount: 193.
Image: vds.exe
...
Monday, March 11, 2013
RuCTF 2013 quals - Forensic 100
task.docx
--------------------------------------------------------------------------------------
Hi, kid!
That 8-symbol password, we were talking
about recently, is exactly the same as the text on the T-shirt of that guy.
--------------------------------------------------------------------------------------First let'ts scan the extracted OLE structures. Then you can see two image files although there is only one image in task.docx.
Finally, just take the image2.jpg to solve this challenge~.
Monday, February 25, 2013
IPv6 in Wireshark
IPv6 address beginning with fe80::.. is used for local network.
http://en.wikipedia.org/wiki/IPv6_address
fe80::/10 — Addresses in the link-local prefix are only valid and unique on a single link. Within this prefix only one subnet is allocated (54 zero bits), yielding an effective format of fe80::/64. The least significant 64 bits are usually chosen as the interface hardware address constructed in modified EUI-64 format. A link-local address is required on every IPv6-enabled interface—in other words, applications may rely on the existence of a link-local address even when there is no IPv6 routing. These addresses are comparable to the auto-configuration addresses 169.254.0.0/16 of IPv4.
You will see strange packets when you open IPv6 pcap files.
Just decode it
1. Decode AS...
2. select 'Network' tap and then IPv6
3. Now we have IPv6's packet streams
Monday, February 18, 2013
[qemu #2] debugging ARM
Launch qemu..
Then connect to qemu (ARM based system) through an ssh tunnel.
ssh User@IP Address -p [port number]
Now you can debug with gdb~
Wednesday, February 13, 2013
[Essay] malcolm gladwell - Outliers '10000 hours rule'
오늘 강연 중에 좋은 말들이 있어서 몇 가지 남겨두려고 한다.
#1 mannerism
많이 들어본 단어인데, 매너리즘... 매너리즘... 위키에서 정의한
매너리즘의 뜻은 아래와 같다.
Mannerism
http://en.wikipedia.org/wiki/Mannerism
그러니깐 매너리즘은 현상 유지하는 상태, 발전이 없는 상태,
, 노력도 하지 않고, 전혀 새로울 게 없는 상태...
이럴 때 우리는 "매너리즘에 빠졌다"라고 말한다.
#2 꿈..?!
George Clooney가 주연한 "Up in the Air"라는 영화,
조지 클루니가 해고 전문가로 등장하는데,
가족을 위해 헌신한 중견 간부를 해고시키는 과정에서 던진 말...
"자신의 꿈을 포기한 대가로 얼마나 벌었습니까?"
'업 인 디 에어' 요거 챙겨봐야지
#3 '10000 hours rule' by malcolm gladwell
한 3년 전쯤 읽었나,,
아직도 기억난다 이 책은,, 아마 집으로 돌아가는 버스 안에서 봤었다
뒷쪽 하차하는 문 바로 뒤에 자리에 앉아서....
이상하게도 기억이 생생하다.
'만 시간의 법칙'
하루 세 시간씩 10년을 하면 만 시간이다
일년은 8,760 시간.. 내 생각엔 매일할 수는 없으니 하루 4시간 씩,
일주일에 적어도 5일 이상은 꾸준히 해야하는 수준일 듯 하다.
이정도면 어느 분야에서건 전문가라는 소리를 듣지 않을까?
Practice makes perfect.
Tuesday, February 12, 2013
[qemu #1] installing on ubuntu 12.04
You can download qemu from the following URL.
http://wiki.qemu.org/Download
extract the package
$ tar -jxvf qemu-1.2.0.tar.bz2
* note
First, I downloaded and installed qemu-1.3.1 in Ubuntu 12.04.
It doesn't work.
(cd /home/.../qemu-1.3.1/pixman; autoreconf -v --install)
/bin/sh: 1: autoreconf: not found
make: *** [/home/.../qemu-1.3.1/pixman/configure] Error 127
http://stackoverflow.com/questions/14814889/cant-install-qemu-1-3-1-in-ubuntu-12-10
$ sudo apt-get build-dep qemu
$ ./configure --target-list=arm-softmmu
$ make
$ make install
will be continued
Wednesday, February 6, 2013
codegate 2012 prequal network 100
자, 패킷 포맷을 제대로 이해했다면 이제 실전에 적용해 보자.
실전에 적용해 보기 위해 아주 좋은 예제가 있다.
코드게이트 2012년 prequal 네트워크 100 문제~
파일 이름은 10_Floor.pcap으로 명명했다.
See on the link below to refer to pcap file format.
http://n20kim.blogspot.kr/2013/02/pcap-file-format.html
Wireshark can't open the pcap file.
If you understand pcap file format, you could notice what is weird.
Yeah, right!
pcap has global header at the beginning of the pcap. :)
# recover the pcap's global header.
1.make global header to add global header to the pcap.
To make this, I made this code. It's simple but entering line by line is a little bit annoying
2. add global header to the pcap
But an error still occurs because of size. phew...
Fix it again!
3. Did you notice something? The problem is size... and 22nd packet is normal.
So you can infer that 23rd packet is probably abnormal.
22nd packet byte streams is following:
4. The last line from 0x0038 is "16 d0 e3 42 ... "
Find that byte streams in the 10_Floor.pcap
23rd packet starts with "3e ec 60 ..".
Packet header has 16bytes as you know.
You can see "GET .." instead of packet header bytes. weird...
 5. The final task is removing 23rd packet. Then you can open the pcap.
5. The final task is removing 23rd packet. Then you can open the pcap.
실전에 적용해 보기 위해 아주 좋은 예제가 있다.
코드게이트 2012년 prequal 네트워크 100 문제~
파일 이름은 10_Floor.pcap으로 명명했다.
See on the link below to refer to pcap file format.
http://n20kim.blogspot.kr/2013/02/pcap-file-format.html
Wireshark can't open the pcap file.
If you understand pcap file format, you could notice what is weird.
Yeah, right!
pcap has global header at the beginning of the pcap. :)
# recover the pcap's global header.
1.make global header to add global header to the pcap.
To make this, I made this code. It's simple but entering line by line is a little bit annoying
import binascii
binary=binascii.unhexlify("d4c3b2a1020004000000000000000000ffff000001000000")
f=open('header.pcap','w')
f.write(binary)
f.close()
2. add global header to the pcap
But an error still occurs because of size. phew...
Fix it again!
3. Did you notice something? The problem is size... and 22nd packet is normal.
So you can infer that 23rd packet is probably abnormal.
22nd packet byte streams is following:
4. The last line from 0x0038 is "16 d0 e3 42 ... "
Find that byte streams in the 10_Floor.pcap
23rd packet starts with "3e ec 60 ..".
Packet header has 16bytes as you know.
You can see "GET .." instead of packet header bytes. weird...
pcap file format
http://wiki.wireshark.org/Development/LibpcapFileFormat#File_Format
패킷 헤더의 구조를 알면 패킷을 분석할 때 유용하다. 잘 알아둘 필요가 있다. wireshark에서 제공하는 문서를 잘 이해해 두기 바란다~
The Libpcap's format is following:
Global header | Packet Header | Packet Data | Packet Header | Packet Data | ...
# Global header has the following structure:

typedef struct pcap_hdr_s {
guint32 magic_number; /* magic number */
guint16 version_major; /* major version number */
guint16 version_minor; /* minor version number */
gint32 thiszone; /* GMT to local correction */
guint32 sigfigs; /* accuracy of timestamps */
guint32 snaplen; /* max length of captured packets, in octets */
guint32 network; /* data link type */
} pcap_hdr_t;
# Record (Packet) Header has the following structure:
typedef struct pcaprec_hdr_s {
guint32 ts_sec; /* timestamp seconds */
guint32 ts_usec; /* timestamp microseconds */
guint32 incl_len; /* number of octets of packet saved in file */
guint32 orig_len; /* actual length of packet */
} pcaprec_hdr_t;
Monday, February 4, 2013
install cx_Oracle on Ubuntu 12.04 or Windows
#1 Windows + cx_Oracle
1) download the Oracle instant client
http://www.oracle.com/technetwork/topics/winsoft-085727.html
2) place it on some directory.
3) Add the directory path to your PATH environment variable
4) run the following code to test
import cx_Oracle
conn = cx_Oracle.connect(ID/PW@DB.com)
#2 Ubuntu 12.04 + cx_Oracle
http://rahadianokta.wordpress.com/2012/09/15/oracle-instant-client-python-cx_oracle-ubuntu-server-12-04/
1) download the Oracle instant client
http://www.oracle.com/technetwork/topics/linuxsoft-082809.html
2) unzip to your lib path
/usr/local/lib/
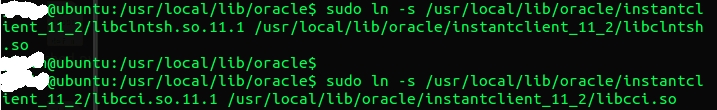
3) soft link libclntsh.so.11.1 to libclntsh.so and libocci.so.11.1 to libocci.so
4) add Oracle instant client path to ld.so.conf.d
# ldconfig
5) edit your system environment variable (/etc/environment)
Finally~~ yeah~
Practical man-in-the-middle attack on pip
I got an interesting article that warns installing packages using pip
in an untrusted environment
You can intercept and manipulate packages downloaded by PyPi
using the below python code
https://gist.github.com/4698537
yeah~ poc time~
Proof Of Concept
1. run a proxy to see all HTTP traffic through the proxy
2. redirect traffic over your local machine
3. intercepts all traffic
4. use the python script to manipulate downloads by PyPi
Wednesday, January 30, 2013
Oracle Tips
#1 list all the tables in a database
-> select * from tab;
#2 check oracle charset
-> select userenv('LANGUAGE') from dual;
#3 sysdate
select XXX from YYY
where Time >= sysdate- INTERVAL '12' hour
#4 to_date
select * from YYY where Time >= to_date('01-02-2013','dd-mm-yyyy');
#5 list all columns
SELECT *
FROM ALL_TAB_COLUMNS
WHERE TABLE_NAME IN (
SELECT TABLE_NAME
FROM ALL_TABLES
WHERE OWNER ='user account')
cx_Oracle...
#1
Problem
ORA-12705: Cannot access NLS data files or invalid environment specified in
ORA-12705: "invalid or unknown NLS parameter value specified"
Cause: There are two possible causes:
- An attempt was made to issue an ALTER SESSION statement with an invalid NLS parameter or value.
- The NLS_LANG environment variable contains an invalid language, territory, or character set.
Solution
putenv("NLS_LANG=KOREAN_KOREA.KO16KSC5601");
putenv("ORACLE_SID=oracle9");
putenv("ORACLE_HOME=D:\oracle\ora92");
putenv("ORA_NLS33=D:\oracle\ora92\ocommon\nls\admin\data");
putenv("TNS_ADMIN=D:\oracle\ora92\network\ADMIN");
linux: export NLS_LANG=KOREAN_KOREA.KO16KSC5601
Windows console : set NLS_LANG=KOREAN_KOREA.KO16KSC5601
LINUX(UTF-8) 시스템 : NLS_LANG=KOREAN_KOREA.AL32UTF8
#2
Problem
UTF-8 Encoding
Solution
# -*- coding: utf-8 -*-
import os
os.environ['NLS_LANG'] = '.UTF8'
con=connet('user/password@ip:port/UID')
con.encoding
Tuesday, January 29, 2013
Review of Hyundai Capital Hacking
Hyundai Capital's information technology systems had been managed by Hyundai Autoever.
Hyundai Capital, the consumer finance unit of Hyundai Motor Group, was leaked personal information on about 420,000 of its 1.8 million customers in 2011.
금융감독원에서 발표한 현대캐피탈 해킹 보도 자료를 살펴보자.
Let's see Korean Financial Supervisory Service's audit report.
-------------------------------------------------------------------------------------------------------------------------
[현대캐피탈 해킹, 금감원 보도 자료]
https://www.google.co.kr/url?sa=t&rct=j&q=&esrc=s&source=web&cd=4&ved=0CFAQFjAD&url=http%3A%2F%2Fwww.claimcare.co.kr%2Fbbs%2Fdownload.php%3Fbo_table%3Dclaim_pds%26wr_id%3D1078%26no%3D0&ei=HIcIUeDPGrHliQKQhoGwAQ&usg=AFQjCNFrYtpoVLWY9OrC7k2EYKL2RpbL3w&sig2=7wfiq94Nqy8Sx4H-X5jSdQ&bvm=bv.41642243,d.cGE&cad=rja
- 사고개요
3월6일~4월7일 해커가 업무관리자의 ID와 비밀번호를 습득한 뒤 보조서버인 광고메일 발송서버와 정비내역 조회서버에 침입해 화면을 복사 또는 해킹프로그램을 설치하고 다운로드하는 방식으로 약 175만명의 고객정보를 해킹했다
* 외부에서 광고메일 발송 서버에 접속한 ID/PW 2개 및 퇴직직원의 ID/PW 1개
- 사고 발생원인
◦ 업무 성격상 불필요한 ID/PW 부여 및 담당직원 퇴직(1명) 후 ID/PW 미삭제**
* 외부에서 광고메일서버에 접속가능한 ID/PW(5개) 부여
** 퇴직직원이 재직시 사용하던 ID/PW로 정비내역조회서버에 총 7회 무단 접속
◦ 해킹침입방지/차단시스템 관리 불철저
* 해킹침입방지시스템이 2.15 ~ 4.6 기간중 해킹사고와 동일한 IP에 의한 해킹시도를 다수 적출하였음에도 해킹패턴 분석 및 해당 IP 접속 차단 등 예방조치 미실시
** 해킹방지 관련 아웃소싱업체와「해킹시도정보 통보기준」을 명확히 정하지 않은 점도 사고원인중 하나
◦ 해킹프로그램 업로드 차단 등 대응조치 미흡
* 해킹파일로 의심되는 확장자(jsp)에 대한 필터링 기능 미비 및 파일 업로드 실행권한 제거 등 대응조치 미실시
◦ 해킹사고 발생시 정보유출을 최소화 할 수 있는 고객 비밀번호 암호화* 및 업무관리자의 화면 조회시 주민번호 뒷자리 숨김표시(*) 미조치 등
* DB서버(메인시스템)내에 보관중인 고객 비밀번호는 암호화하고 있으나, 고객정보 조회․생성․변경사실 등이 기록되는 로그파일에 남아있는 고객 비밀번호 암호화는 미실시
-------------------------------------------------------------------------------------------------------------------------
Hackers only need to find one weakness to exploit, online service providers need to find and fix them.
[Suspected hacker in Hyundai Capital incident arrested in the Philippines.]
http://cybersecurityidiots.wordpress.com/2011/10/23/suspected-hacker-in-hyundai-capital-incident-arrested-in-philippines/
Thursday, January 24, 2013
[python] spidermonkey #1
Hi,
Have you used [SpiderMonkey] which is Mozilla's JavaScript engine?
[SpiderMonkey]
https://developer.mozilla.org/en/docs/SpiderMonkey
[python-spidermonkey]
http://pypi.python.org/pypi/python-spidermonkey
[ref]
http://pydermonkey.googlecode.com/hg/docs/rendered/pydermonkey.htmlhttp://code.google.com/p/python-spidermonkey/
[Code Snippet]
# -------------------------------
# run a JavaScript file
# -------------------------------
import spidermonkey
runtime = spidermonkey.Runtime()
context = runtime.new_context()
f = open("path",'r')
script = f.read()
context.eval_script(script)
Subscribe to:
Comments (Atom)